Is your Office 365 configured securely?
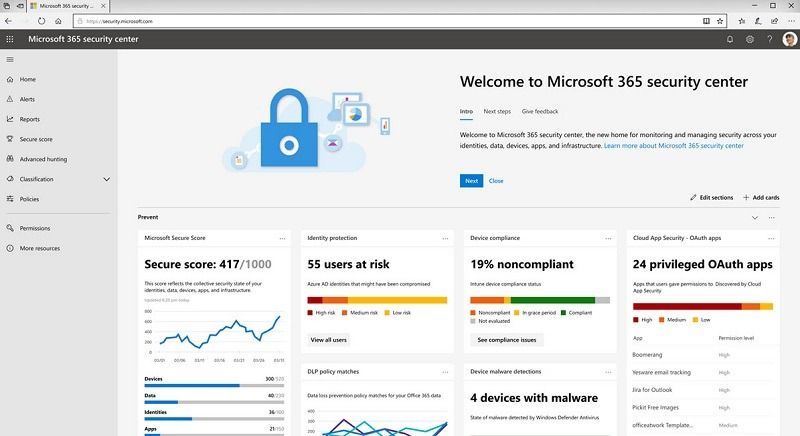
Security experts, including Microsoft and the US Cybersecurity and Infrastructure Agency (CISA), are warning organisations that have migrated their email services to Office 365 to check their configuration and apply five critical configuration changes to reduce potential security risks such as identity theft or other digital fraud.
ID Integrated Data SA strongly encourages companies to implement a secure cloud strategy to protect their infrastructure assets by defending against attacks related to their O365 transition and securing their O365 service. In particular, CISA and Microsoft recommend that IT administrators implement the following mitigation measures and best practices to secure your data hosted by Microsoft, including Exchange Online, SharePoint Online, Teams, and OneDrive.
1. Use multi-factor authentication. This is the best mitigation technique to use to protect O365 users from credential theft.
Administrator accounts are particularly vulnerable because they are cloud-based. The basics of multi-factor authentication are included in Office 365 (free), but advanced features are supplemented with Azure Active Directory Premium.
2. Enable unified audit logging in the Security and Compliance Centre
The unified audit log contains events from Exchange Online, SharePoint Online, OneDrive, Azure AD, Microsoft Teams, PowerBI, and other O365 services. An administrator must enable the unified audit log in the Security and Compliance Centre before queries can be run. Once auditing is enabled, you can configure threat detection settings and emails to receive security alerts. Threat detection detects abnormal activities that indicate potential threats to database security. This allows you to detect potential threats and respond to them as they arise.
3. Enable mailbox auditing for each user
Office 365 mailbox auditing records actions performed by mailbox owners, delegates, and administrators. This information can be critical for preventing and investigating email security breaches.
4. Ensure that Azure AD password synchronisation is scheduled and configured correctly before migrating users
Azure AD Connect integrates on-premises environments with Azure AD when customers migrate to O365. When Azure AD is configured with the ‘Password Sync’ option, the local Azure AD password overwrites the Azure AD password. In this particular situation, if the on-premises AD identity is compromised, an attacker could move laterally to the cloud when synchronisation occurs. When configured correctly, admin accounts cannot be hacked to compromise all cloud data.
5. Disable existing messaging protocols if they are not required, or restrict their use to specific users.
A number of protocols associated with Exchange Online authentication do not support modern authentication methods with MFA capabilities and are therefore less secure. These protocols include POP3 (Post Office Protocol), IMAP (Internet Message Access Protocol), and SMTP (Simple Mail Transport Protocol). Where possible, disable these legacy protocols that do not support modern authentication. Doing so will significantly reduce the attack surface for organisations.
Do you need help securing your O365 data? Let our team of IT infrastructure and data protection experts help you take immediate steps to secure your Microsoft Office 365 cloud data. We have long-standing expertise and apply best practices to ensure the security of your data and that of your organisation. Contact us today!